These are abstract ideas. More research and tests will be needed to determine the effectiveness of this project.
The problem?
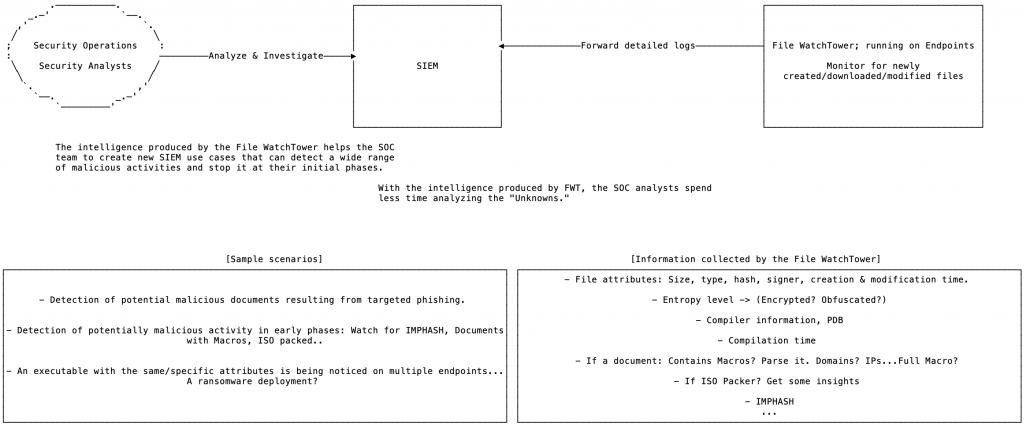
- SOCs analysts spend time analyzing the “Unknowns.”
- Lack of sufficient intelligence about new files causes slow response and can lead to other higher risks; compromise, post-exploitation, and other malicious activities.
File WatchTower — The Early radar
A tool continuously monitors newly created/modified and downloaded files on the OS and reports detailed logs to other security systems/tools such as SIEM.
The intelligence produced by the File WatchTower helps the SOC team to create new SIEM use cases that can detect a wide range of malicious activities and stop it at their initial phases.
With the intelligence produced by FWT, the SOC analysts spend less time analyzing the “Unknowns.”
Information collected by the File WatchTower
- File attributes: Size, type, hash, signer, creation & modification time.
- Entropy level -> (Encrypted? Obfuscated?)
- Compiler information, PDB
- Compilation time
- If a document: Contains Macros? Parse it. Domains? IPs…Full Macro?
- If ISO Packer? Get some insights
- IMPHASH
- More..
Sample usage scenarios
- Detection of potential malicious documents resulting from targeted phishing.
- Detection of potentially malicious activity in early phases: Watch for IMPHASH, Documents with Macros, ISO packed..
- An executable with the same/specific attributes is being noticed on multiple endpoints… A ransomware deployment?
